Real Talk
Networking is somehow simultaneously overpromoted and severely underutilized.
In some ways, you might feel like it’s too late to start growing a network on LinkedIn, and perhaps you have reconciled with the fact that expanding your connections beyond the same 50 people, half of whom are your childhood friends, maybe a distant cousin or two, and what’s-his-face from your first job at that one Italian restaurant – would probably prove to be pretty helpful. Maybe you’ve hit a wall – or thought it was useless or a waste of time up until this point because “it’s just social media,” “it’s just a popularity contest,” and in all honesty, I don’t disagree with you. Some of you may find it daunting, and it might remain a love-hate relationship with this platform.
But the truth is, “Oh wow, you know so-and-so! Now I feel a little bit more comfortable connecting with you –” is essentially the name of the game. That and learning to nurture a genuine curiosity for people to approach you first or feel inclined to respond to you. There’s a reason why LinkedIn URLs are so highly requested on job applications. A recruitment survey led by The Manifest in 2020 corroborates this as covered by PR Newswire:
❝ 67% of companies look at job candidates’ LinkedIn profiles ❞
Given my personal experience of monitoring who has viewed my profile, I’d have to agree, particularly for positions in specialized fields – like cybersecurity, of course. Whether we like it or not, point #1 is to widen your network: this helps to establish a degree of confidence in reaching out. Point #2 – deepen your network: build degrees of interconnection and become the next familiar name and face to a future connection or in a job hunt.
Welcome to “LinkedIn networking” at its bare-bones.
Having signed up for a LinkedIn account way back in June of 2013, teetering a sliver over 10 years of on and off trial and error with both basic and premium membership tiers throughout the years, I hope that this will provide you with a bit of useful insight.
If someone needs this reminder right now, here it is:
Be mindful and be considerate through it all. Don’t be a(n) _________.
The Why
#1 It Turns Out That People Actually Pay Attention
- Think: can they hear what I would sound like while reading this?
- Will they hypothetically be able to answer: “what do you remember about this candidate that we’re interested in hiring?” or “would you walk up to say ‘hello’ if you saw them at a conference?”
#2 Sometimes It’s What You Say, Mostly It’s How You Say It
- Hey Michelle – it was so nice to chat and get to know you at X Conference! Would greatly appreciate keeping in touch, and I’m excited to follow more of your content on LinkedIn. Thanks so much!
- Good seeing you at X Conference. Looking forward to keeping in touch. Thanks.
- Do take advantage of the filters available, such as sorting by “latest” posts or discovering thought leaders with certain hashtags or keywords listed on their headlines.
- Your intention for outreach may be good, but the questions, comments or messaging might sound… unintentionally obtuse.
- Ex: don’t make others do your work and answer your “answerable” questions for you. I say this fully knowing that information overload is a very real thing, but Google should and will be your best friend. Learning to ask informed questions is an invaluable skill.
- Some people just aren’t responsive and choose not to be, or they’re selective and that’s valid. Let them be. Nobody owes you a response.
#3 Oh Right, And It Certainly Matters When You Say It
- Magnifies the likelihood of people seeing your face pop up [first] in the comments and clicking on your profile.
- Increases the likelihood of people requesting to connect with you after looking at your profile and your super cool bio.
- Most definitely increases the chances of growing your network → higher probability of future mutual connections with someone else that you would want to connect with.
So – What Exactly Happened & How Did It Work Out?
“Examples or It Didn’t Happen.”
#1
#2
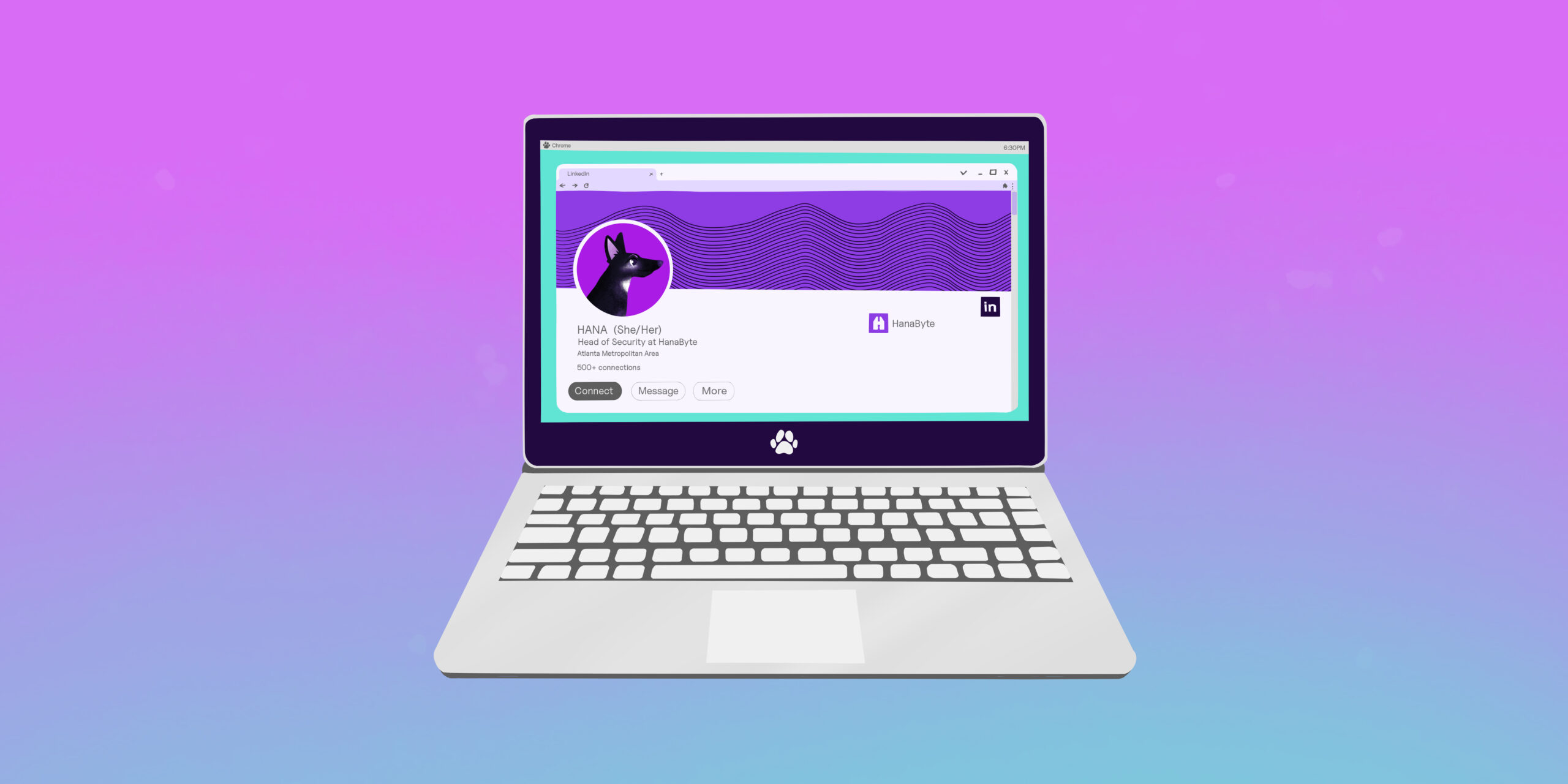
There is an awesome connection that I made back when I first started my deep dives into all things cybersecurity, and we will call her Bon Qui Qui for the sake of this blog (because “saCURRRRITY”).
It might’ve been an update to Bon Qui Qui’s new job or some kind of announcement post on my newsfeed as I was scrolling as usual, but I noticed an individual and company name (in the headline) within the congratulatory comments thread that I hadn’t seen before.
Sound the alarms! This was a new degree of connections in the making – and a magnificent German Shepherd was sitting as Head of Security.
To clarify, I’m an ardent believer of multilingualism’s power to deepen empathy and understanding in individuals, allowing more doors to open in creative thinking, collaborating, and strategizing.
Upon some casual sleuthing, I quickly noticed that the CEO, Kat Evans, spoke both Thai and Lao (and Japanese!) – and having lived in Laos for some time and fallen in love with Southeast Asia – I felt an instant connection. We all know that tech (and cyber) can feel a bit homogeneous, so I was elated to find a diverse team and quite frankly, the most impressive ratio of polyglot employees that I’ve ever seen in one organization.
Imagine endlessly wandering and feeling extremely homesick – and then reaching a familiar and inviting doorstep.
That’s what this felt like and I knew I had to stay in touch.
Nearly four months later at the time of writing this, I have no doubt in my mind that I fully optimized LinkedIn as the tool that it was meant to be to find my place in cybersecurity. It was thanks to that one Bon Qui Qui post and a comment left in the thread by the one and only CTO of HanaByte, Eric Evans.